 Last Thursday, the US Supreme Court approved a new rule that would make it easier for law enforcement agencies including the FBI to hack any computer, regardless of its location. This decision will take effect from December unless the Congress opts to bring up a competing legislation against the decision. The FBI will have the powers to search any computer (even those that are remotely located) that has online anonymity software installed in it. The new ruling also allows the FBI to hack into computers that have been hacked once or those infected by a botnet, which is a type of malware program that takes over many computers and infect them with viruses.
Last Thursday, the US Supreme Court approved a new rule that would make it easier for law enforcement agencies including the FBI to hack any computer, regardless of its location. This decision will take effect from December unless the Congress opts to bring up a competing legislation against the decision. The FBI will have the powers to search any computer (even those that are remotely located) that has online anonymity software installed in it. The new ruling also allows the FBI to hack into computers that have been hacked once or those infected by a botnet, which is a type of malware program that takes over many computers and infect them with viruses.
Beware Online Anonymity Seekers
Federal judges would now be able to issue search warrants that would allow law enforcement agents to search or seize any computer anywhere. The rule also incorporated a small paragraph that is related to computers using privacy software. According to approved change to Rule 41, a federal magistrate judge has the power to issue a search/seizure warrant for any computer anywhere in the world that uses online anonymity tools like VPN and Tor. The US Supreme Court has purportedly approved the rule change to combat the rising incidents of cyber-crime. Interestingly, this rule was approved just a day after advancement of a bill by the US House of Representatives that made it a prerequisite for the government to obtain a judge’s cause warrant before seizing stored data from company computers such as Dropbox, Facebook or Google.
John Roberts, Chief Justiceof the Supreme Court,submitted the rule change to Congress as part of the annual collection of amendments to the Federal Rules of Criminal Procedure.Kevin Bankston, Open Technology Institute director (policy advocacy group) opined that the changed rule would authorize much more of government hacking than what is happening currently. He urged the Congress to pose questions to the FBI in this regard. It is alleged that FBI is fighting cases in court to keep its spying tactics a secret from the public.
As a deviation from the current Rule 41 which allows a magistrate judge to issue search warrants only within their jurisdictions, the amended rule would allow the same magistrate judge to issue search/seize warrants on any computer if its location has been hidden through technical means.It is also possible for the government to search millions of computers all at once with just a single warrant. There was added concern that the computers searched would belong to the victims of the cyber-crime that seek online anonymity instead of the perpetrators in most cases.
Whereas many of the experts that testified against such changes of the rule and privacy advocates are smarting against the upper handedness of the government, many are calling on the Congress to reject the rule that could mean an end to online anonymity. Senator Ron Wyden, an advocate of privacy, added that the amendment was clearly a debate that the Congress and the elected representatives of the country should take up and resolve after adequate public vetting. This is important in the light of the fact that there are over a million people that use Tor and other online anonymity tools for very legitimate reasons just as some others are using it to hide their crimes.
 Absence of any opposition to the rule means that it will come into effect in December this year and will result in spying by the government on users of Tor or VPN services without the user having any knowledge of it. The Department of Justice, however, welcomed the amendment. Their argument was that this change would help to prosecute those criminals that use Tor or similar tools to maintain online anonymity while perpetrating their crimes.
Absence of any opposition to the rule means that it will come into effect in December this year and will result in spying by the government on users of Tor or VPN services without the user having any knowledge of it. The Department of Justice, however, welcomed the amendment. Their argument was that this change would help to prosecute those criminals that use Tor or similar tools to maintain online anonymity while perpetrating their crimes.
Earlier in the month, an Oklahoma federal judge had to turn down evidence in a case relating to child pornography owing to the limitations of Rule 41. Though the amendment to Rule 41 was proposed in the year 2015 by the Department of Justice, Google, in collaboration with other privacy advocacy groups wrote a letter expressing concerns about the violations of international agreements that this amendment would bring about as a result of the authorization of the government to conduct searches on computers outside of the United States.







 Some might say “About time!” because earlier this year one of the darknet markets, Agora, “retired” from business claiming that they have found a glitch in Tor’s security system and decided to wait some time until this is fixed.
Some might say “About time!” because earlier this year one of the darknet markets, Agora, “retired” from business claiming that they have found a glitch in Tor’s security system and decided to wait some time until this is fixed.
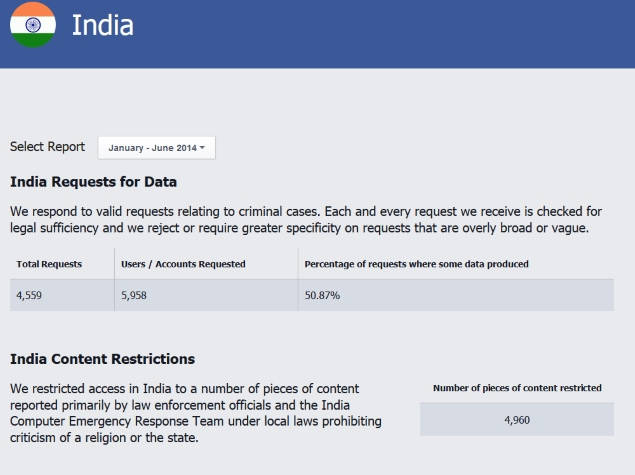
 The metadata retention scheme is a mandatory retention of data by telecommunication companies, internet service providers from their customers. The new law will require the companies to develop systems that will be used to store their customer’s data for two years. The data stored will be accessible to law enforcement agencies without the need for a warrant.
The metadata retention scheme is a mandatory retention of data by telecommunication companies, internet service providers from their customers. The new law will require the companies to develop systems that will be used to store their customer’s data for two years. The data stored will be accessible to law enforcement agencies without the need for a warrant.
 Tor is an online anonymity tool that encrypts the traffic going from your computer and bounces it through several servers around the world to mask your location. It is available free of charge, and is easily downloaded and installed on your computer. However, it can lead to latency issues. It can also make you a target of law enforcement agencies, since there have been quite a number of cases where criminals use it to hide their activities.
Tor is an online anonymity tool that encrypts the traffic going from your computer and bounces it through several servers around the world to mask your location. It is available free of charge, and is easily downloaded and installed on your computer. However, it can lead to latency issues. It can also make you a target of law enforcement agencies, since there have been quite a number of cases where criminals use it to hide their activities.

 Working in close collaboration, behavioral biometrics and behavioral profiling precisely draft your online portfolio, making it easier to keep tabs on you as soon as you start typing and speaking online from a certain location; your facial features are analyzed as well. Whereas behavioral biometrics are based on subtle nuances in your typing patterns, voice, location and special features, behavioral profiling track your online presence after having analyzed your behavior. Each needs the other to accomplish what many loath; shatter your online anonymity without remorse. No one is in the clear when it comes to behavioral profiling.
Working in close collaboration, behavioral biometrics and behavioral profiling precisely draft your online portfolio, making it easier to keep tabs on you as soon as you start typing and speaking online from a certain location; your facial features are analyzed as well. Whereas behavioral biometrics are based on subtle nuances in your typing patterns, voice, location and special features, behavioral profiling track your online presence after having analyzed your behavior. Each needs the other to accomplish what many loath; shatter your online anonymity without remorse. No one is in the clear when it comes to behavioral profiling. The GREYC lab researchers have portrayed consistency in the results brought forth by their algorithm. Your keystrokes are not a rigid structure and from time to time, there will be considerable differences. Even then, the graphs used in identifying your online presence remain largely uniform, distinguishing you from anyone else whose behavioral traits seem to match yours. Just like fingerprints were and still are used for identification, this evolved to DNA and now keystrokes are beckoning to be the leading identifier online; the possibilities which this technology can unleash are limitless, especially in the cybercrimes units. Online anonymity may have been assured by private window browsing’ or application of passwords a few years ago but think again; the playing field has drastically changed and is no longer level.
The GREYC lab researchers have portrayed consistency in the results brought forth by their algorithm. Your keystrokes are not a rigid structure and from time to time, there will be considerable differences. Even then, the graphs used in identifying your online presence remain largely uniform, distinguishing you from anyone else whose behavioral traits seem to match yours. Just like fingerprints were and still are used for identification, this evolved to DNA and now keystrokes are beckoning to be the leading identifier online; the possibilities which this technology can unleash are limitless, especially in the cybercrimes units. Online anonymity may have been assured by private window browsing’ or application of passwords a few years ago but think again; the playing field has drastically changed and is no longer level.