Fifty years ago, people would have considered WiFi(or Wireless Fidelity)a miracle—a discovery that they couldn’t possibly have any explanation for.
However, slowly but surely, scientists and engineers started dreaming actively about something so amazing, yet far-fetched.
Only a few years later, those once unattainable dreams became a reality. Because of these brave dreamers, people today have access to the internet everywhere.
Today, we use the word WiFi to refer to the devise that allows computers, smartphones and other gadgets to connect to the internet and communicate wirelessly.
Continually, it seems to be almost everywhere these days. People are worried or worst upset when they enter a coffee shop or a mall that does not provide Wireless Internet. Furthermore, public or private users can enjoy the following properties of wireless connection.
- Efficiency – It has never been easier to transfer information in such a great speed. Businesses can transfer their data from one place to another in a matter of seconds.
- Flexibility – One does not have to be at the office to receive important business information, which means, information or data can be sent or received by anyone anywhere
- Cost Effectiveness – Given that people spend hundreds or thousands of dollars on things they may or may never use, it is considered to be wallet-friendly and also a smart investment.
- Accessibility – It would be safe to say that this technology has become somewhat a necessity over the last two decades. Needless to say, most public places intends to cater the needs of the people, which means that most of them (if not all of them) now provide Wireless Internet connection.

Two types of WiFi
Most of us are exposed to the technology of the 21stcentury, the Internet know that there is a public and a private/home WiFi.
Consequently, it is fairly easy to extrapolate that public WiFi can be found in public places, such as shops, malls, cafes, bars, restaurants, and even playgrounds in city parks.
On the other hand, private refers to the wireless connection set up for a private user at one’s home or a private office.
Public WiFi (Pros and Cons)
As the name suggests, this internet connection is available for the public to use, or anyone who desires to connect to the Internet in public places such as airports, libraries, hotel lobbies or a café.
One of its major pros is that it is free and people do not have to worry about spending money to check their emails, communicate via Skype or transfer important information.
However, there is one major drawback to public wireless connection and that is WiFi Security.
WiFi Security
Unfortunately, using a public connection will put your computer at risk and your personal data very vulnerable.
This could be extremely dangerous when the user shares sensitive information, such as personal information, passwords or bank account details.
Hackers, in this case, are much harder to detect, because more often than not, they use the same network as their “prey”.
Subsequently, insufficient WiFi Security can cause myriads of problems, such as identity-theft, loss of funds and destruction of important information.
Government authorities in charge of street WiFi, and other owners of this public amenity are aware of this dire problem and are purportedly looking into finding a solution for inadequate WiFi Security.

One way to improve Public WiFi Security is by implementing VPN—a Virtual Private Network is one key to a successful WiFi Security, its purpose is to encrypt data that make interception impossible.
Public users can also implement WPA/WEP which encodes data that is being transmitted between a user’s computer and the wireless router.
Subsequently, even though the hacker may get into one’s system, they will not be able to decrypt and interpret the information.
Pros and Cons of a Public WiFi
| Pros | Cons |
| It is easy to access | Insufficient WiFi Security measures |
| Multiple users | Slower speed |
| Internet on the go | Needs additional VPN for better WiFi Security |
| It is free | Needs additional WPA or WEP for better WiFi Security |
| Does not require a password | If hacked due to insufficient WiFi Security, the party-to-blame is hard to locate |
How to Detect If You Are Being Snooped On In Public WiFi
Accessing an open network with low (or no) WiFi Security puts the user at risk of being hacked. In other words without WiFi Security while using a public connection puts you at a higher risk that someone nearby will have access to your personal information.
Even though this may sound like an exciting science fiction movie, rest assured that it is our reality today, and if we are not careful enough, a “snooper” can surprise us at any local café, a hotel lobby or even the kids’ playground.
Fortunately, users can now take the following steps and attain a few helpful tools to detect if their data is being observed by unwanted parties.
- Turn on Your Firewall
- Turn Off Sharing
- Use HTTPS and SSL Whenever Possible
- Turn it Off When You Aren’t Using It
- Download Free Who’s On My WiFi Windows, Mac, or Android
- Detection Agent
- Download Wifi SPY Android app
- CyberGhost VPN
- Hide My Ass (HMA)
- TunnelBear
- OkayFreedom VPN
Home or Private WiFi
Home or Private WiFi is a facility that is available in one’s home or private business for their personal use of the Internet.
This does not necessarily mean that other users cannot connect to the internet using a Private connection, but unlike public WiFi, the private one requires a password.
This naturally leads us to conclude that it offers greater Security measures than its public counterpart.
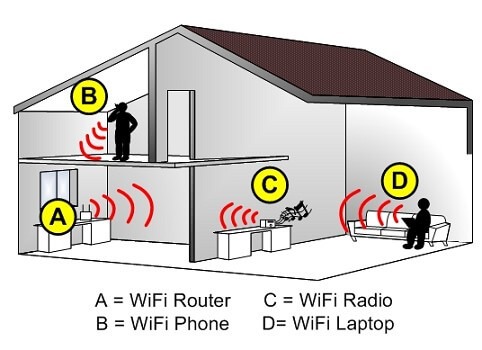 First and foremost, setting up a private WiFi is very easy, which means you do not need the assistance of a professional since you are probably more than capable to do it yourself.
First and foremost, setting up a private WiFi is very easy, which means you do not need the assistance of a professional since you are probably more than capable to do it yourself.
Furthermore, one major and very important difference between a public and private WiFi is that the latter automatically encrypts outgoing and incoming messages which provides data security.
This way, individuals may it be a small business owner, an important CEO or just a stay-at-home mom who wants to surf the Internet need not worry about their personal emails or bank accounts being hacked due to an already embedded high WiFi Security.
Pros and Cons of a Home/Private WiFi
| Pros | Cons |
| High WiFi Security | It can only be accessed within private premises |
| Due to its great WiFi Security, home WiFi requires a password, which means not everyone can access it | Installation problems may occur, though it is not very likely to happen. |
| It is inexpensive | Individuals (guests/employees) can only use it if the password is provided |
| Higher Internet Speed | |
| It is easy to set up |
Conclusion
The truth is, this facility has become a daily necessity. Without such in this fast-paced technological era would be unimaginable.
However, even though this indispensable facility may have a few cons, such as insufficient WiFi Security, the various pros will serve as a testament on how important it is in our daily endeavors.
Overall, since its discovery in 1991, Wireless Fidelity has drastically changed the way we transfer information, conduct business deals and communicate with each other.
In addition to that, it would be safe to say it made life more convenient and changed our daily routine for the better.
Thus, whether you are a private or a public user, the one little catch to look out for is WiFi Security.





 What many didn’t realize is the smart move by the Department of Defense to use the newly updated strategy to openly attempt to reduce the level of Internet anonymity that is often enjoyed online.
What many didn’t realize is the smart move by the Department of Defense to use the newly updated strategy to openly attempt to reduce the level of Internet anonymity that is often enjoyed online.
 Like your wallet, your device contains private information including credit card and bank account numbers or other financial details. Due to the lack of internet security and anti-virus app installed on your smartphone, it is a vulnerable target for hackers other than computers, laptops and tablets. Once you’ve been caught off guard and your device has been infiltrated by hackers, they can either steal your personal information or infect your smartphone with viruses like malicious software or malware, which slows down any devices’ system and speed.
Like your wallet, your device contains private information including credit card and bank account numbers or other financial details. Due to the lack of internet security and anti-virus app installed on your smartphone, it is a vulnerable target for hackers other than computers, laptops and tablets. Once you’ve been caught off guard and your device has been infiltrated by hackers, they can either steal your personal information or infect your smartphone with viruses like malicious software or malware, which slows down any devices’ system and speed.



 To protect your online personal information and
To protect your online personal information and