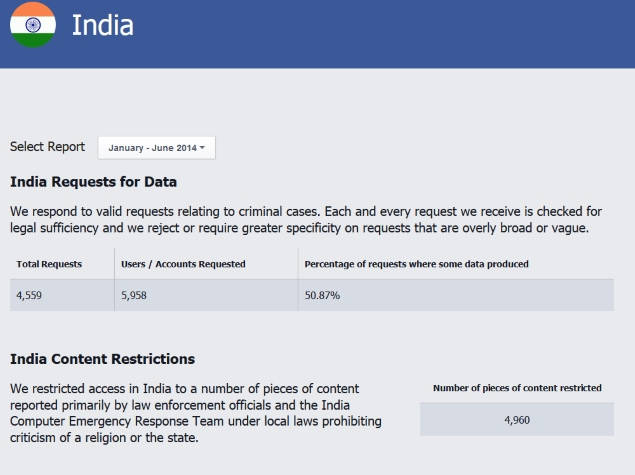
Cyber-attacks have been on the rise and it has negatively affected many big companies. TalkTalk is one of the recent victims whereby personal data of about 4 million of its customers was stolen. However, studies were conducted regarding online security and the results showed that there is a bigger risk to online security apart from cyber crime.
The Department for Business, Innovation and Skills (BIS) commissioned PricewaterhouseCoopers (PwC) to conduct a survey on incidents of cyber security across companies in the UK. The survey was aimed at creating awareness among UK businesses of the risks and key trends. PwC released a report which showed that security breaches that are staff related has risen to 75%. The previous year, only 58% of large companies were affected. Small businesses were not left out as 31% also suffered security breaches that were staff related. This is an increase from the previous year where only 22% of small businesses were affected.
Businesses that took part in the survey were questioned about the worst breach they had suffered and 50% of them said their worst breaches were caused by human error. This is an increase from the 31% that was recorded the previous year. The cost of these incidents has also doubled causing some to change the nature of their businesses. The report also stated that incidents of human error were “near certainty.” They advised businesses to ensure their defenses kept pace with the Internet security threats.

Apart from PwC, CheckRecipient also conducted its own research. CheckRecipient is a cyber security company and it works with law firms in the UK to ensure sensitive information is not emailed to the wrong person. The report showed that in 2014, 9% of the data security incidents reported was as a result of human error. This is higher than intentional cyber espionage that accounts for 0.8% of the data security incidents. The CEO of CheckRecipient, Tim Sadler, was surprised that not much attention was being given to the inside Internet security threat faced by most companies.
Security breaches caused by human error can be categorized into 3 parts and PwC reported on how each part was affected. They include:
1.Breach of laws and regulations that govern data protection. In 2014, 45% of such incidents occurred while in 2015, the incidents increased to 57%.
2.Unauthorized access to systems or data. 57% of such incidents occurred in 2014 but in 2015, they rose to 65%.
3.Loss or leakage of financial information. These incidents rose from 55% in 2014 to 66% in 2015.
Morrisons is one of the companies that suffered an incident related to personal data loss of its customers. Andrew Skelton who was a senior internal auditor in the head office at Bradford, received discipline for conducting eBay deals using the company’s postroom. Due to this, he got through company controls, obtained and leaked data that contained dates of birth, national insurance numbers, bank account details and salaries of nearly 100,000 employees. The information was sent to various newspapers. He was later sentenced to 8 years in jail. It costs Morrisons more than 2 million pounds to deal with the problem.

Despite the company’s efforts and Andrew Skelton being jailed, some 2000 current and former employees of the company have sued the company due to the leaked information claiming that the company had the responsibility of keeping such information confidential. Morrisons refused to accept liability for the actions of Andrew Skelton. The spokesman of the company also said the company was not aware of anyone who suffered financial loss from the breach.
In PwC’s report, it was noted that some of the Internet security incidents were as a result of giving low priority to security, poorly understood Internet security policies and lack of briefing company boards of security risks. Companies that had faced such problems suffered more security breaches compared to those that gave Internet security high priority, trained their staff on Internet security and briefed the board of the company about any security risks the company faces.
As Internet security threats increase due to human error, both small and large companies should focus on dealing with this Internet security threat first as it costs a lot of money to control the damage. After that, other Internet security threats can be focused on.